Overview
This guide details the necessary steps to establish SSO for Amazon Web Services using BeanLogin.
The guide assumes that you already have an existing AWS subscription.
| Create As Password-Vault App | Create As SAML App | User Provisioning Supported |
| Supported | Supported | Not Supported |
SSO Configuration in AWS
Pre-requisites
- Administrator credentials to your organization’s AWS console.
- Metadata File from BeanLogin.
- Login to BeanLogin as an Administrator.
- Navigate to Administration >> Access Management >> Corporate Apps.
- Click New.
- Select AWS from the list of apps and click it will give option whether to add as password-vault/SAML based on choice select the proper option and click on Add Selected Apps. It will add apps under corporate section with status as inactive
- Go through the configuration wizard and download the metadata file. This is required to configure SSO within AWS.
Configure BeanLogin as IdP within AWS
- Login to AWS console, then select Services.
- Click IAM under Security and Identity Compliance.
- Select Identity Providers menu from the left hand pane.
- Select Create Provider.
- In the Configure Provider screen, enter the following:
- Provider Type: Select SAML from the dropdown menu.
- Provider Name: BeanLogin.
- Metadata Document: Upload the metadata document provided by BeanLogin. You will be able to get this through the BeanLogin Admin UI.
- Click Next. Click Create.
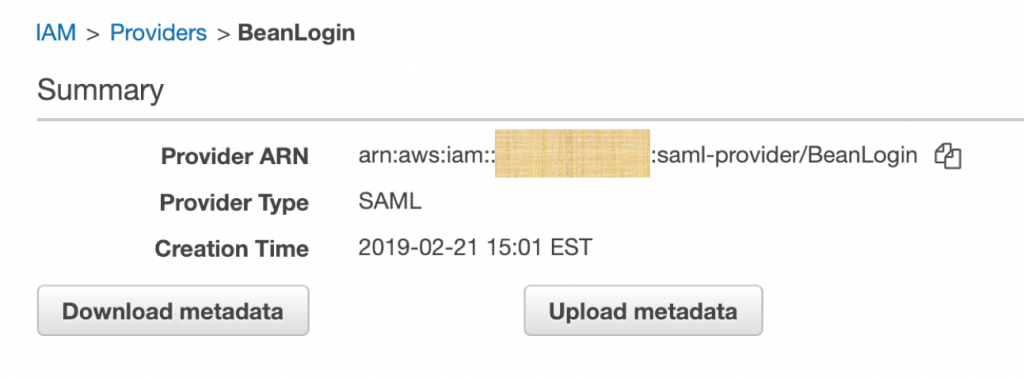
- Once created successfully, you can see the summary as below.
Create a SAML role that can be used by BeanLogin Users
- Now that you have added BeanLogin as an Identity Provider within AWS, you can create or update existing IAM roles to trust this newly created Identity provider.
- Navigate to Roles >> Create New Role.
- Select SAML 2.0 Federation and choose BeanLogin as the Identity Provider.
- Check Allow programmatic and AWS Management Console access.
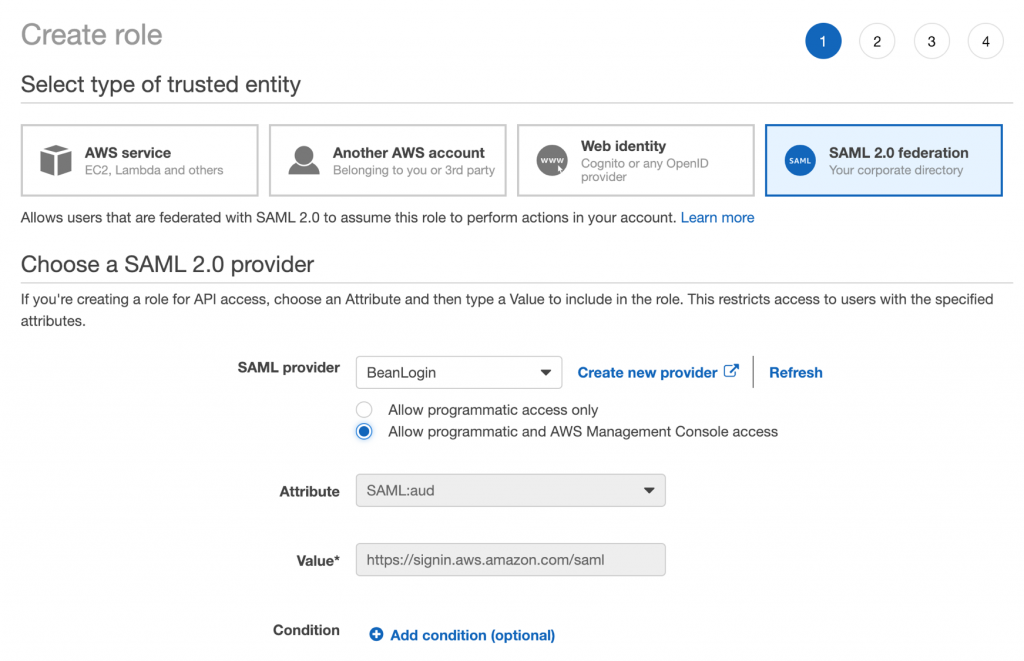
- Scroll through the configuration wizard and select your preferred policy for the federated users.
Configuration within BeanLogin
Create Custom User Fields
AWS requires two mandatory user attributes to be passed in the SAML Assertion. These must be created within BeanLogin as custom user fields.
- Login to BeanLogin as an Administrator.
- Navigate to Administration >> Identity Management >> Custom User Fields.
- Click New.
- Create two attributes with the following info:
- Attribute1
- Friendly Name: Role
- Claim Name: https://aws.amazon.com/SAML/Attributes/Role
- Attribute2
- Friendly Name: RoleSessionName
- Claim Name: https://aws.amazon.com/SAML/Attributes/RoleSessionName
- Attribute1
- Click Save.
Update Role and RoleSessionName for Users
Now that we have created the attributes, we need to make sure we populate these attributes with the right values for the users.
- Login to BeanLogin as an Administrator.
- Navigate to Administration >> Users.
- Select a user and update the field values as below.
- Role: <user’s email>
- Example: john@apollomon.com
- RoleSessionName: arn:aws:iam::<provider-id>:role/<role-name>,arn:aws:iam::<provider-id>:saml-provider/<provider-name>
- Example: arn:aws:iam::123456789:role/SAMLRole,arn:aws:iam::123456789:saml-provider/BeanLogin
- Role: <user’s email>
- You can find the Role ARN and Provider ARN in the summary of Provider and Role respectively within AWS IAM configuration screen.
Pass Role & RoleSessionName within SAML Assertion
- Login to BeanLogin as an Administrator.
- Navigate to Administration >> Access Management >> SSO Apps.
- Select AWS.
- Click Advanced Mode.
- Go to Step-2: Authentication & Authorization.
- Select the Attributes – Role & RoleSessionName.
- Click Next.
- Click Submit.
You are now ready to test AWS SSO by clicking the app icon from the User Portal.